WASHINGTON, D.C. -- One of the most recent examples of a data security breach receiving widespread visibility in the U.S. is the Heartbleed bug that affected the credit and debit cards of millions of American shoppers earlier this year. A little less than half of Americans (45%) say they are aware of the bug, but of those who are aware, 71% are "somewhat" to "very concerned" about the security of their personal information. Even then, about four in 10 of those aware have not taken any specific action as a result.

These data are from an April 23-29 Gallup survey.
Numerous websites and online retailers, including some household names like Google, Yahoo, and Amazon, were identified in news reports as particularly vulnerable to the Heartbleed bug first publicized on April 7, but believed to have been in existence for about two years. The Heartbleed bug is a flaw in commonly used data encryption methods that hackers can exploit to gather personal information.
Those Contacted by Websites/Online Retailers Mostly Changed Passwords
Many of the larger and better-known companies took immediate action to block the threat by patching their systems. But just 35% of respondents who were aware of the bug reported having received any communication from the companies they do business with about the threat or their response to it. While concern is high for those aware of Heartbleed, being contacted directly by a website or online retailer doesn't appear to have prompted additional action to mitigate the risk other than a greater propensity to change passwords.
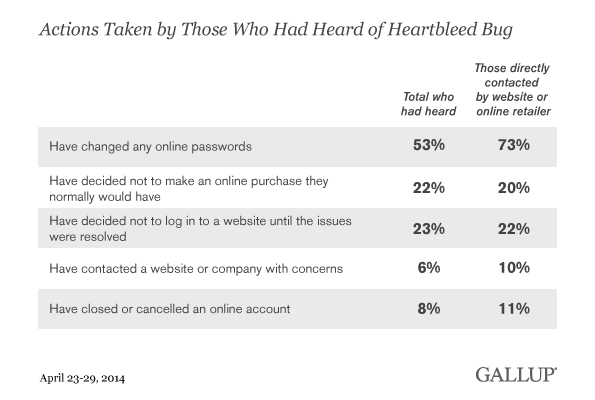
Among those who were contacted directly by a website or online retailer, 73% changed at least one of their online passwords, substantially higher than those who were not directly contacted (43%). Other responses to the bug did not differ as a function of being contacted. One plausible reason for the difference on passwords but not on other precautions may be that the communication customers received generally reminded them to change their passwords, but otherwise indicated that the website was not vulnerable to the bug or that the company had already taken steps to update and fix its systems to ameliorate the threat.
Implications
In spite of considerable coverage of the Heartbleed bug in news stories and online media, less than half of all Americans are aware of the issue. Even fewer received any sort of notification about the bug from websites or online retailers that they use. Most of those who did receive notification followed the advice commonly given in this situation and changed their passwords. Yet less than 50% of this group took any other specific action, such as delaying a purchase or contacting the website or retailer with a concern. These results are virtually identical to what consumers who knew about the bug but received no notification did.
What do these findings mean? Have Americans become so accustomed to data breaches that they feel they are inevitable? This kind of "learned helplessness" could surely result in a failure to act. Individuals and companies alike can take steps to ensure at least a minimum level of additional online security.
These steps may include websites being engineered to require password changes every so often for continued access. This is the norm for most corporate networks and, as a proactive measure, could minimize the consequences of a future Heartbleed-type event. Companies can also take more aggressive measures to contact users when a security breach occurs. If it is assumed that those who were unaware of the Heartbleed bug had not been contacted directly by a website or online retailer, just 16% of Americans received any notification about the bug at all.
But consumers must also bear some of the responsibility for the security of their information. Exercising reasonable vigilance by practicing basic security precautions can reduce the risk of one's personal information being compromised. Changing passwords, not using the same password on multiple online accounts or websites, and using strong but memorable passwords are simple steps that all consumers can take.
Survey Methods
Results for this Gallup poll are based on telephone interviews conducted April 23-29, 2014, on the Gallup Daily tracking survey, with a random sample of 1,011 adults, aged 18 and older, living in all 50 U.S. states and the District of Columbia.
For results based on the total sample of national adults, the margin of sampling error is ±4 percentage points at the 95% confidence level.
Interviews are conducted with respondents on landline telephones and cellular phones. All interviews were conducted in English. Each sample of national adults includes a minimum quota of 50% cellphone respondents and 50% landline respondents, with additional minimum quotas by time zone within region. Landline and cellular telephone numbers are selected using random-digit-dial methods. Landline respondents are chosen at random within each household on the basis of which member had the most recent birthday.
Samples are weighted to correct for unequal selection probability, nonresponse, and double coverage of landline and cell users in the two sampling frames. They are also weighted to match the national demographics of gender, age, race, Hispanic ethnicity, education, region, population density, and phone status (cellphone only/landline only/both, and cellphone mostly). Demographic weighting targets are based on the most recent Current Population Survey figures for the aged 18 and older U.S. population. Phone status targets are based on the most recent National Health Interview Survey. Population density targets are based on the most recent U.S. census. All reported margins of sampling error include the computed design effects for weighting.
In addition to sampling error, question wording and practical difficulties in conducting surveys can introduce error or bias into the findings of public opinion polls.
For more details on Gallup's polling methodology, visit www.gallup.com.
